Kendall and Kendall Systems Analysis and Design Solutions Manual

16 Kendall & Kendall Systems Analysis and Design, 9 e Quality Assurance and Implementation Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall

Learning Objectives • Recognize the importance of users and analysts taking a total quality approach to improve the quality of software design and maintenance. • Realize the importance of documentation, testing, maintenance, and auditing. • Understand how service-oriented architecture and cloud computing is changing the nature of information system design. Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -2

Learning Objectives (continued) • Design appropriate training programs for users of the new system. • Recognize the differences among physical conversion strategies, and be able to recommend an appropriate one to a client. • Address security, disaster preparedness, and disaster recovery concerns for traditional and Web-based systems. • Understand the importance of evaluating the new system, and be able to recommend a suitable evaluation technique to a client. Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -3

Major Topics • • Six Sigma Quality assurance Walkthroughs Structure charts Modules Documentation Testing Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -4

Major Topics (continued) • • Client-server computing Network types Groupware Training Security Organizational metaphors Evaluation Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -5

Six Sigma • • • A culture built on quality Uses a top-down approach Project leader is called a Black Belt Project members are called Green Belts Master Black Belts have worked on many projects and are available as a resource to project teams Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -6
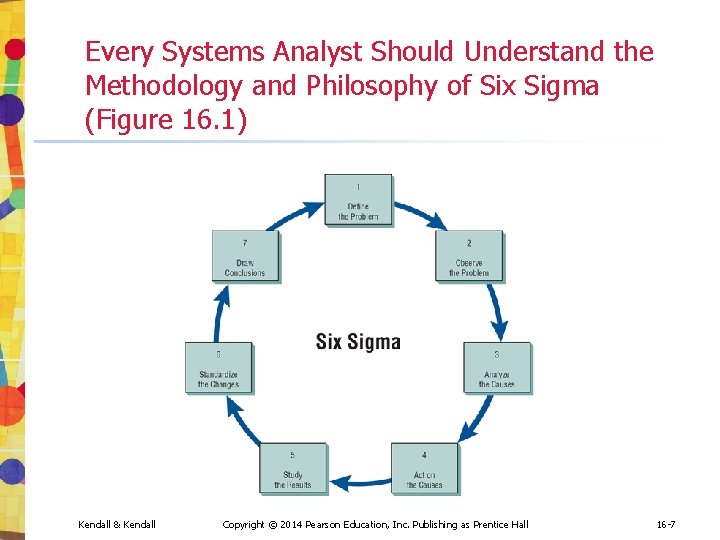
Every Systems Analyst Should Understand the Methodology and Philosophy of Six Sigma (Figure 16. 1) Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -7

Responsibility for Total Quality Management • Full organizational support of management must exist • Early commitment to quality from the analyst and business users Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -8

Structured Walkthroughs • One of the strongest quality management actions is to do structured walkthroughs routinely • Use peer reviewers to monitor the system's programming and overall development • Point out problems • Allow the programmer or analyst to make suitable changes Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -9

Involved in Structured Walkthroughs • The person responsible for the part of the system being reviewed • A walkthrough coordinator • A programmer or analyst peer • A peer who takes notes about suggestions Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -10

The Top-Down Approach • Top-down design allows the systems analyst to ascertain overall organizational objectives and how they are best met in an overall system • The system is divided into subsystems and their requirements Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -11
Advantages of the Top-Down Approach • Avoiding the chaos of attempting to design a system all at once • Enables separate systems analysis teams to work in parallel on different but necessary subsystems • Prevents losing sight of what the system is suppose to do Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -12
Modular Development • Breaking the programming into logical, manageable portions or modules • Works well with top-down design • Each individual module should be functionally cohesive, accomplishing only one function Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -13
Advantages of Modular Programming • Modules are easier to write and debug • Modules are easier to maintain • Modules are easier to grasp because they are self-contained subsystems Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -14
Guidelines for Modular Programming • Keep each module to a manageable size • Pay particular attention to the critical interfaces • Minimize the number of modules the user must modify when making changes • Maintain the hierarchical relationships set up in the top-down phases Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -15
Using Structure Charts to Design Systems • The recommended tool for designing a modular, top-down system is a structure chart • A structure chart is simply a diagram consisting of rectangular boxes, representing the modules, and connecting lines • Hollow circle arrows represent data being passed up and down the structure • Filled-in circle arrow represents a control switch or flag Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -16
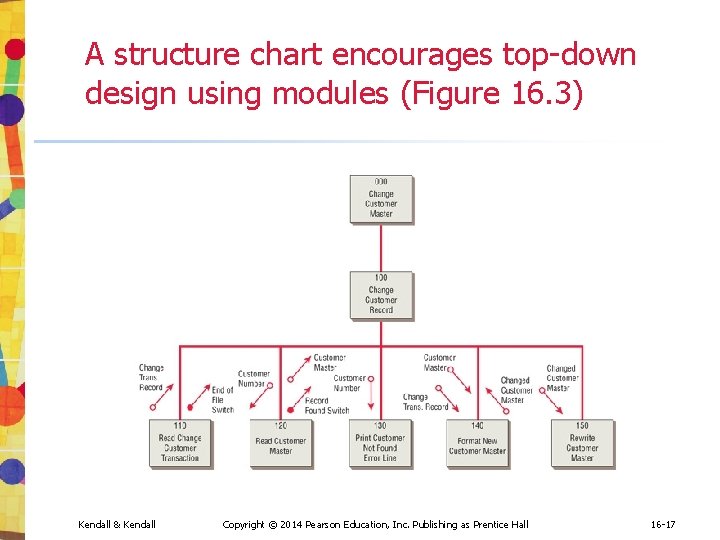
A structure chart encourages top-down design using modules (Figure 16. 3) Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -17

Service Oriented Architecture (SOA) • The SOA approach is to make individual SOA services that are unassociated or only loosely coupled to one another • Each service executes one action • Each service can be used in other applications within the organization or even in other organizations Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -18
Service Oriented Architecture (SOA) (continued) • A service can use certain defined protocols so that it can communicate with other services • The burden of connecting services in a useful fashion, is a process called orchestration • This can even be accomplished by selecting services from a menu of services and monitoring them by setting up an SOA dashboard Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -19
Service Oriented Architecture (SOA) (continued) • In order to set up a SOA, services must be: • Modular • Reusable • Work together with other modules (interoperability) • Able to be categorized and identified • Able to be monitored • Comply with industry-specific standards Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -20
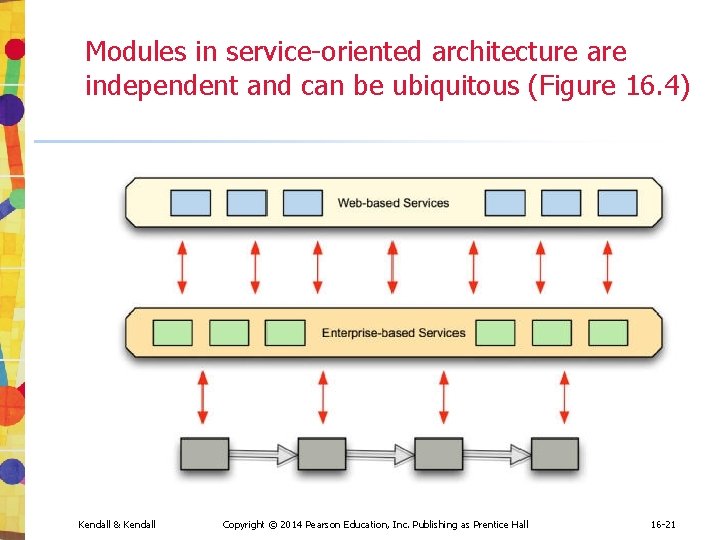
Modules in service-oriented architecture are independent and can be ubiquitous (Figure 16. 4) Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -21
System Documentation • Procedure manuals • The FOLKLORE method Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -22
Procedure Manuals • The English-language component of documentation • Key sections: • • • Kendall & Kendall Introduction How to use the software What to do if things go wrong A technical reference section An index Information on how to contact the manufacturer Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -23

Procedure Manuals (continued) • Procedure manual complaints: • They are poorly organized • It is hard to find needed information • The specific case in question does not appear in the manual • The manual is not written in plain English Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -24
The FOLKLORE Method • Collects information in categories: • • Kendall & Kendall Customs Tales Sayings Art forms Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -25

Customs, Tales, Sayings, and Art Forms Used in the FOLKLORE Method of Documentation Apply to Information Systems (Figure 16. 5) Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -26
Choosing a Design and Documentation Technique • Is it compatible with existing documentation? • Is it understood by others in the organization? • Does it allow you to return to working on the system after you have been away from it for a period of time? Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -27
Choosing a Design and Documentation Technique (continued) • Is it suitable for the size of the system you are working on? • Does it allow for a structured design approach if that is considered to be more important than other factors? • Does it allow for easy modification? Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -28
Testing, Maintenance, and Auditing • The testing process • Maintenance practices • Auditing Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -29
The Testing Process • • Program testing with test data Link testing with test data Full system testing with live data Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -30
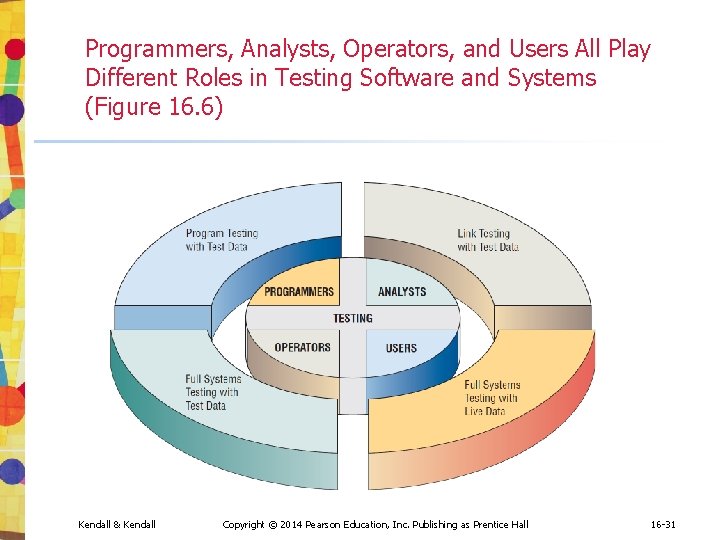
Programmers, Analysts, Operators, and Users All Play Different Roles in Testing Software and Systems (Figure 16. 6) Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -31
Program Testing with Test Data • Desk check programs • Test with both valid and invalid data • Check output for errors and make any needed corrections Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -32
Link Testing with Test Data • Also referred to as string testing • Checks to see if programs that are interdependent actually work together as planned • Test for normal transactions • Test with invalid data Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -33
Full System Testing with Test Data • Adequate documentation in procedure manuals • Are procedure manuals clear enough? • Do work flows actually "flow"? • Is output correct and do users understand this output? Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -34
Full System Testing with Live Data • Comparison of the new system's output with what you know to be correctly processed output • Only small amounts of live data are used Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -35

Maintenance Practices • Reduce maintenance costs • Improve the existing software • Update software in response to the changing organization • Ensure channels for feedback Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -36

Auditing • Having an expert who is not involved in setting up or using the system examine information in order to ascertain its reliability • There are internal and external auditors • Internal auditors study the controls used in the information system to make sure that they are adequate • External auditors are used when the information system processes data that influences a company's financial statements Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -37
Implementing Distributed Systems • Can be conceived of as an application of telecommunications • Includes work stations that can communicate with each other and with data processors • May have different hierarchical architectural configurations of data processors that communicate with one another Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -38
Client-Server Technology • The client-server model refers to a design model that can be thought of as applications running on a network • The client is a networked computer that uses small programs to do front-end processing, including communicating with the user Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -39
Client-Server Model Advantages, Disadvantages • Advantage—greater computer power and greater opportunity to customize applications • Disadvantage—more expensive and applications must be written as two separate software components each running on separate machines Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -40
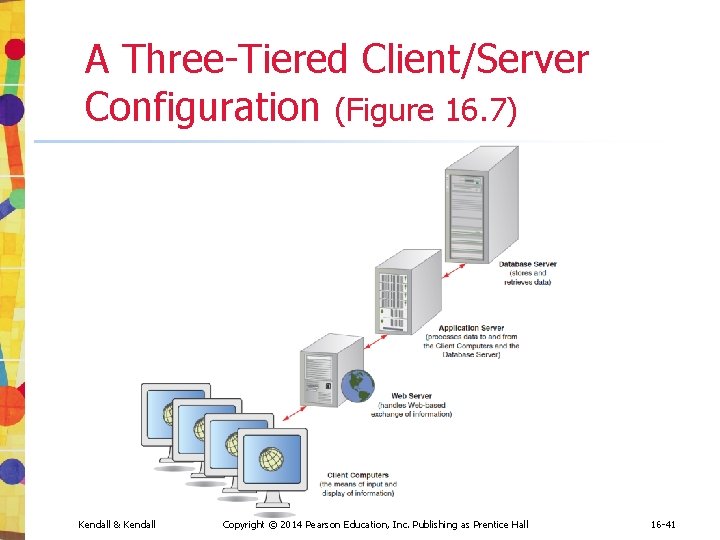
A Three-Tiered Client/Server Configuration (Figure 16. 7) Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -41
Cloud Computing • Organizations and individual users can use: • Web services • Database services • Application services over the Internet • Done without having to invest in corporate or personal hardware, software, or software tools Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -42
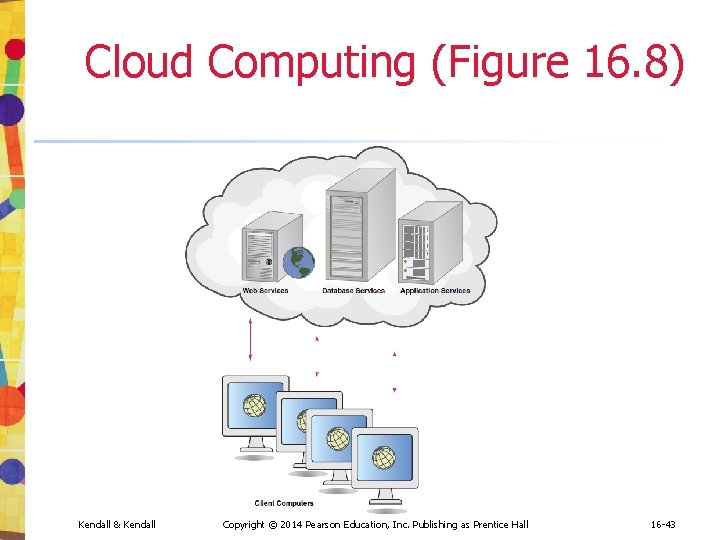
Cloud Computing (Figure 16. 8) Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -43
Cloud Computing • A large collection of corporate users jointly bear the lowered cost • Realize increases in peak-load capacity • Companies also hope to improve their ability to perform disaster recovery Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -44

ERP and Cloud Computing • Many of the issues and challenges associated with implementing ERP systems can be mitigated by ERP offerings that take advantage of cloud computing Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -45
Network Modeling • Draw a network decomposition diagram to provide an overview of the system • Draw a hub connectivity diagram • Explode the hub connectivity diagram to show the various workstations and how they are connected Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -46
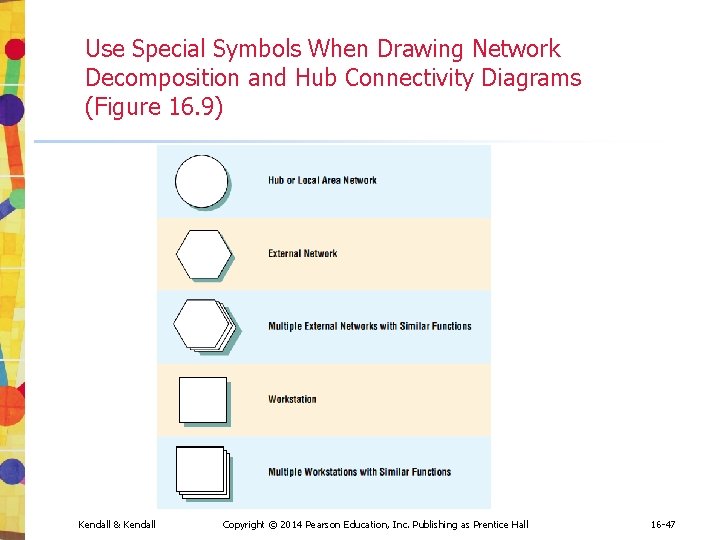
Use Special Symbols When Drawing Network Decomposition and Hub Connectivity Diagrams (Figure 16. 9) Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -47
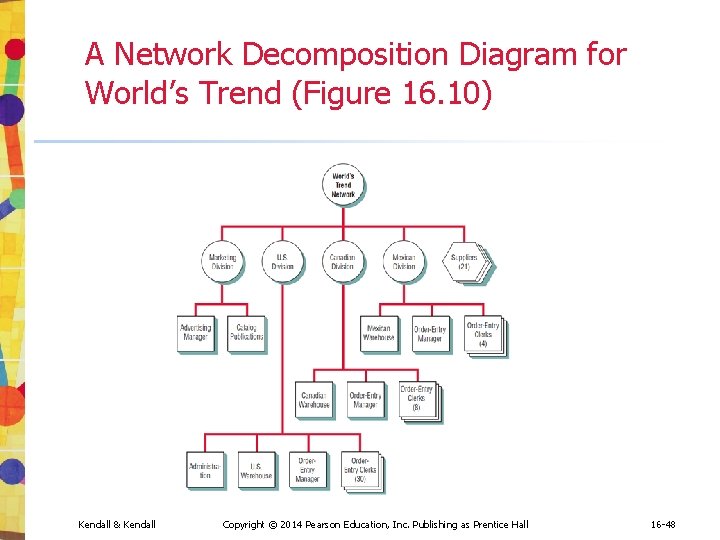
A Network Decomposition Diagram for World's Trend (Figure 16. 10) Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -48
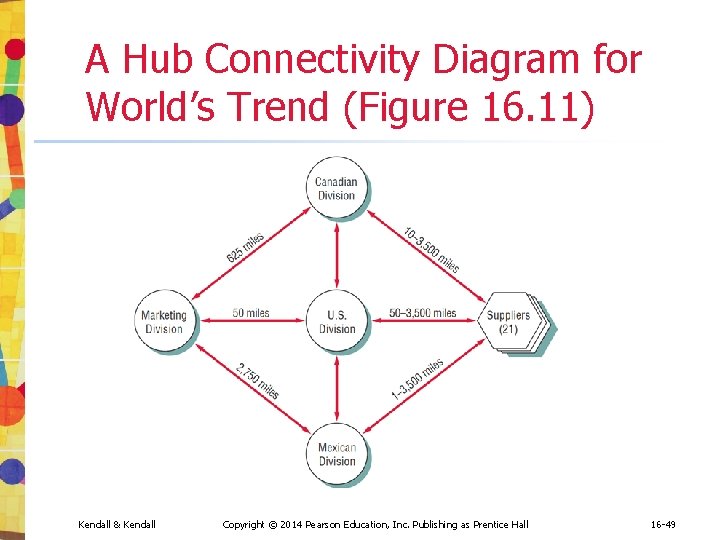
A Hub Connectivity Diagram for World's Trend (Figure 16. 11) Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -49
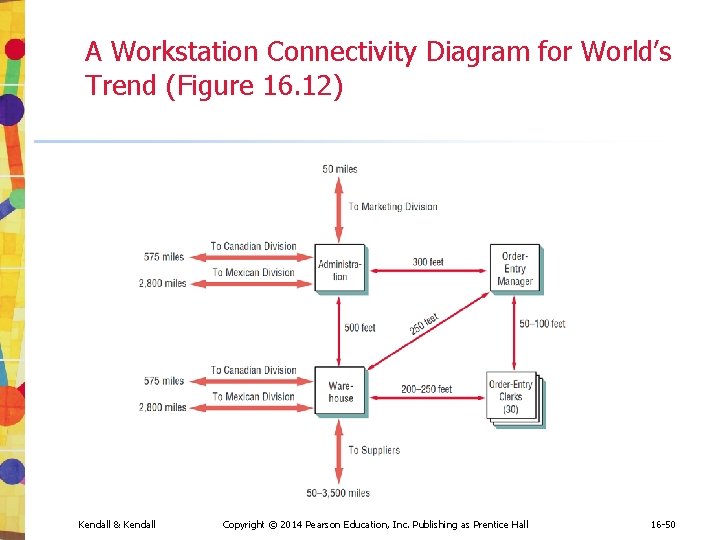
A Workstation Connectivity Diagram for World's Trend (Figure 16. 12) Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -50

Training • • • Who to train People who train users Training objectives Training methods Training sites Training materials Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -51

Who to Train • All people who will have primary or secondary use of the system • Ensure that users of different skill levels and job interests are separated Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -52
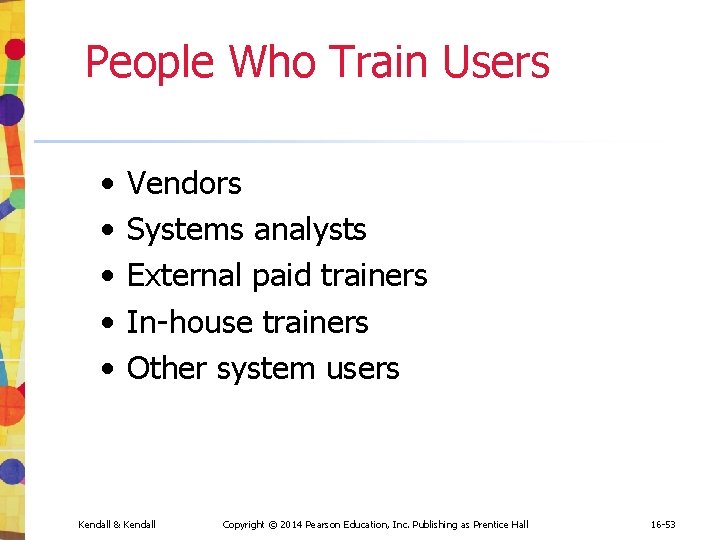
People Who Train Users • • • Vendors Systems analysts External paid trainers In-house trainers Other system users Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -53
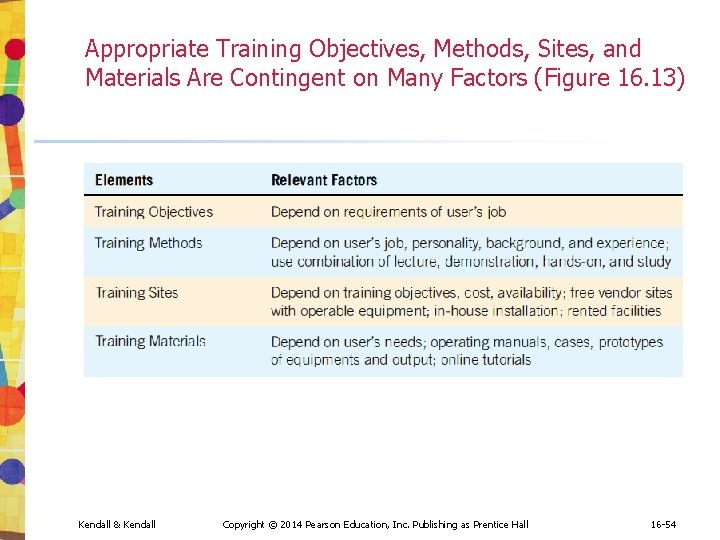
Appropriate Training Objectives, Methods, Sites, and Materials Are Contingent on Many Factors (Figure 16. 13) Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -54
Conversion Strategies • • • Direct changeover Parallel conversion Gradual or phased conversion Modular prototype conversion Distributed conversion Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -55
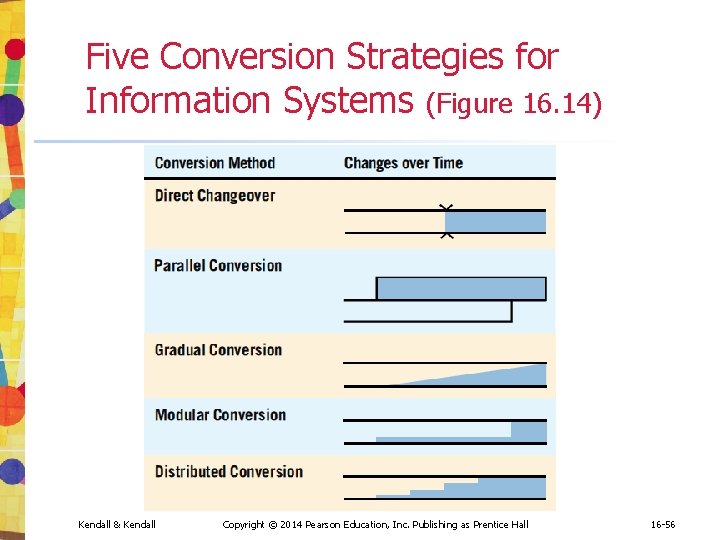
Five Conversion Strategies for Information Systems (Figure 16. 14) Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -56

Direct Changeover • • Old system stops, new one starts Needs extensive testing Risky approach to conversion Users may resent being forced into using an unfamiliar system without recourse • No adequate way to compare new results to old Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -57
Parallel Conversion • Run the old and new systems at the same time • The advantage is that you can check new data against old data • The disadvantage is doubling employees' workloads Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -58
Gradual Conversion • Combines best features of parallel and direct conversion • Volume of transactions is gradually increased • Advantage is that users get involved with the system gradually • Agile methodologies use this conversion approach Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -59
Modular Prototype Conversion • Each module is tested and put into use • The advantage is that each module is thoroughly tested before being used • Users are familiar with each module as it becomes operational • Object-oriented methodologies often use this approach Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -60

Distributed Conversion • When there are many installations of the same system, such as at branch offices • Install software at one office • Advantage is that problems can be detected and contained • Disadvantage is that even when one conversion is successful, each site will have its own peculiarities to work through Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -61
Other Conversion Considerations • Ordering equipment • Ordering any external materials supplied to the information system • Appointing a manager to supervise the preparation of the installation site • Planning, scheduling, and supervising programmers and data entry personnel Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -62
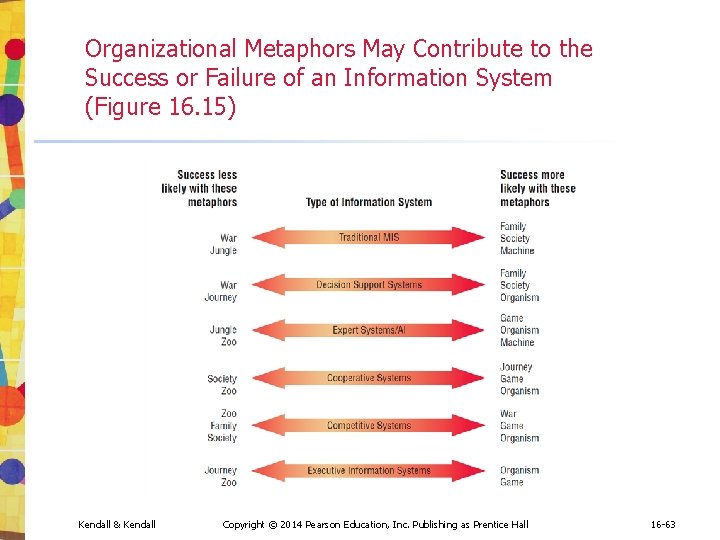
Organizational Metaphors May Contribute to the Success or Failure of an Information System (Figure 16. 15) Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -63

Security Concerns • Physical security • Logical security • Behavioral security Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -64

Security Concerns (continued) • Physical security is securing the computer facility, its equipment, and software through physical means • Logical security refers to logical controls in the software itself • Behavioral security is building and enforcing procedures to prevent the misusing of computer hardware and software Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -65

Special Security Considerations for Ecommerce • • Virus protection software Email filtering products URL filtering products Firewalls, gateways, and virtual private networks • Intrusion detection products Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -66

Special Security Considerations for Ecommerce (continued) • Vulnerability management products • Security technologies such as secure socket layering (SSL) for authentication • Encryption technologies • Public key infrastructure (PKI) use and obtaining a digital certificate Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -67

Privacy Considerations for Ecommerce • Start with a corporate policy on privacy • Only ask for information required to complete the transaction • Make it optional for customers to fill out personal information on the website Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -68

Privacy Considerations for Ecommerce (continued) • Use sources that allow you to obtain anonymous information about classes of customers • Be ethical Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -69

Disaster Recovery Planning • Identify teams responsible for managing a crisis • Eliminate single points of failure • Determine data replication technologies that match the organization's timetable • Create detailed relocation and transportation plans Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -70

Disaster Recovery Planning (continued) • Provide recovery solutions that include an off-site location • Ensure the physical and psychological well-being of employees and others Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -71

Identify Who Is Responsible • Whether business operations will continue • How to support communications • Where people will be sent if the business is uninhabitable • Where personnel will go in an emergency • Seeing to the personal and psychological needs • Restoring the main computing and working environments Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -72
Single Points of Failure and Data Replication Technologies • Redundancy of data provides the key for servers running Web applications • SNAs and data mirroring Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -73

Relocation and Transportation Plans • Send employees home • Remain on site • Relocate to a recovery facility Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -74

Communication Channels • • Email Emergency information Web page Emergency hotline Emergency response agencies Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -75

Recovery Solutions and Support for the Well-Being of Employees • Recovery involves an off-site location and converting paper documents to digital formats • Well-being of employees might include providing water or safety kits Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -76
Evaluation Techniques • • Cost-benefit analysis Revised decision evaluation approach User involvement evaluations The information system utility approach Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -77
Information System Utility Approach • • • Possession Form Place Time Actualization Goal Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -78
Information System Utility Approach (continued) • Possession utility answers the question of who should receive output • Goal utility answers the why of information systems by asking whether the output has value in helping the organization achieve its objectives • Place utility answers the question of where information is distributed Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -79
Information System Utility Approach (continued) • Form utility answers the question of what kind of output is distributed to the decision maker • Time utility answers the question of when information is delivered • Actualization utility involves how the information is introduced and used by the decision maker Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -80

Website Evaluation • Know how often the website is visited • Learn details about specific pages on the site • Find out more about the website's visitors Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -81

Website Evaluation (continued) • Discover if visitors can properly fill out the forms you designed • Find out who is referring website visitors to the client's site • Determine what browsers visitors are using • Find out if the client's website visitors are interested in advertising Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -82
Summary • TQM • Designing systems and software with a topdown, modular approach • Designing and documenting systems and software using systematic methods • Testing systems and software so that they can be easily maintained and audited Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -83
Summary (continued) • Six Sigma • • Kendall & Kendall Define the problem Observe the problem Analyze the causes Act on the causes Study the results Standardize the changes Draw conclusions Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -84
Summary (continued) • • • Structure charts Procedure manuals FOLKLORE Testing System maintenance Auditing Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -85
Summary • Implementation • Distributed systems • Client-server • Training users and personnel • Conversion • • • Kendall & Kendall Direct changeover Parallel Phased Gradual Modular prototype Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -86
Summary (continued) • Security • Physical • Logical • Behavioral • Organizational metaphors • Evaluation Kendall & Kendall Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -87

Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall 16 -88
Kendall and Kendall Systems Analysis and Design Solutions Manual
Source: https://slidetodoc.com/16-kendall-kendall-systems-analysis-and-design-9/